
Growing management liability exposures and rising claims have increased the focus on effective D&O policies backed by effective D&O insurance carriers, ensuring company directors and officers are adequately covered for these risks.

Growing management liability exposures and rising claims have increased the focus on effective D&O policies backed by effective D&O insurance carriers, ensuring company directors and officers are adequately covered for these risks.

In October, the Talbot Underwriting Crisis Management team was delighted to welcome brokers to a breakfast briefing to hear from Product Recall experts.

The AIG team attended the Broker Expo 2025 in Birmingham – one of the UK’s premier one-day event for the insurance broker community, attended by over a 1,000 insurance professionals to connect, collaborate and uncover new business opportunities.

In September, Talbot Underwriting had the pleasure of hosting the third edition of Talbot’s Annual Broker Golf Day at the award winning Westerham Golf Club, Kent, UK.
A celebratory seven four-ball format marked a milestone at Royal Porthcawl in Wales.

Elle Ayton works as an Underwriter within our Financial Lines, Directors & Officers (D&O) Insurance team and has been named Young Achiever of the Year at the British Insurance Awards 2025, held at the Royal Albert Hall in London.

AIG recently attended the Association of Insurance and Risk Managers in Industry and Commerce (AIRMIC) conference in Liverpool. Over three days, AIG UK, Global Specialty and Talbot Underwriting colleagues engaged in meaningful conversations with clients and brokers, deepened partnerships and explored ways to prepare for complex risks.
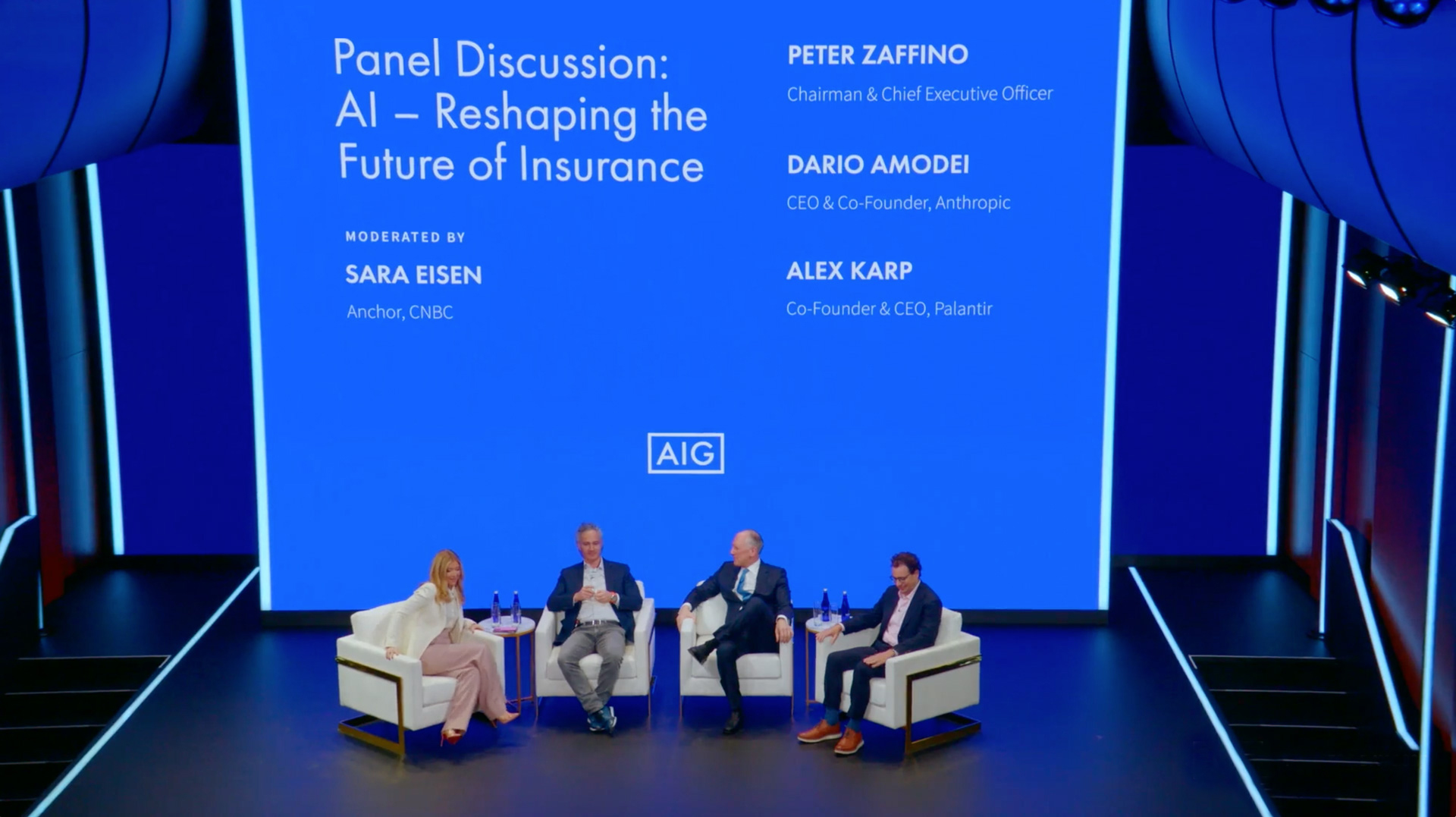
At AIG’s 2025 Investor Day, Chairman and CEO Peter Zaffino was joined by Anthropic Co-founder and CEO Dario Amodei and Palantir Co-founder and CEO Alex Karp for a discussion on how GenAI is reshaping the future of insurance.

AIG UK, Talbot and Lex London have together ensured that AIG has maintained its top five rank on Insurance Post’s Top 100 UK Insurers List for 2024.

In honour of International Day of Persons with Disabilities, AIG celebrates colleagues like Alex Gibson, whose dedication and resilience reminds us why AIG values professionals of all abilities.

Darren Hulst - Vice President - Commercial Marketing, Boeing - shares his insights on innovation in aviation, low cost carrier business models, the connectivity with global economic development and the future of ultra long haul flying, in a conversation with John Strickland.

The Ukraine War marks a watershed in the deployment of sanctions. For the first time, G7 allies targeted a large economy; in addition to having the world’s eighth largest nominal GDP, Russia is a major global commodity exporter with a global footprint. The sanctions imposed on Russia since February 2022 were not just greater in scale and scope than those imposed previously, but different in kind. But how much of an innovation were they, and what clues do they offer for the future role of sanctions as a tool of policy?

Thanks to rapid developments in maritime technology, autonomous shipping is now a realistic possibility. The impact will be wide-ranging, affecting communication and data transfer at sea, route optimisation, regulation and liability, the role of crews and even the definition of “seamanship”.
In this podcast Stavros Karamperidis and expert guests discuss the balance between benefits and risks of autonomous shipping for the maritime sector.

Álex Cruz – Vice Chair, WestJet – gives his perspective on evolving airline business models, the impact of niche technologies, and competitors beyond the airline industry, in a conversation with John Strickland.

Both the digital transition and decarbonisation ambitions have heightened demand for specialty metals, including nickel and lithium for electric vehicles and rare earths for advanced microelectronics. But as advanced economies’ access to these metals is becoming increasing critical, supply security concerns are increasing: production of critical metals is concentrated in a small number of locations, while geopolitical tensions are rising.

Digitally delivered services have experienced a four-fold increase in value since 2005 and now account for a significant share of all services exports. At a time of growing concern about the slowdown in global trade in goods, the boom in digital services trade is a comparative bright spot.

Alan Joyce – Businessman and Former CEO, Qantas – speaks with John Strickland about the dynamics of city pairings and hubs, long haul markets, and the industry innovating to overcome sustainability challenges.

Four years on from Britain’s departure from the EU, politicians on both sides of the Channel continue to grapple with its consequences. What are the political and economic parameters within which the UK and EU are working on a reset? Where are the red lines and where the areas of Win-Win? And can a new deal help address the growth challenge on both sides of the Channel?

In a world of complex digital transformation, shipping faces new threats from organised crime. In this episode, Stavros Karamperidis and guests explain the risks and how the industry is responding.

With global commerce and global trade reliant on complex supply chains, countries can be dependent on a limited number of producers and suppliers. But at what point does over-dependence become a problem? What can organisations do to manage these dependencies against a background of geopolitical risk and policy instability?

Pieter Elbers - CEO of IndiGo – talks to John Strickland about leading India's largest airline, and shares insights on the relationship between aviation and economic growth, including the impact of the subcontinent's expanding hubs and gateways.
While the BJP fell short of an overall majority in India’s recent parliamentary elections, Prime Minister Narendra Modi is set for a third consecutive term – but this time as part of a coalition government. This is uncharted territory for the world's most populous country. How might this new political constellation affect India's economic and geopolitical decision-making? And what does the new political environment in Delhi mean for India's attractiveness as a destination for companies and investors looking to de-risk from China?

With Elvire Fabry (Senior Research Fellow, Jacque Delors Institute) and Miguel Otero Iglesias (Senior Analyst, Elcano Royal Institute), in conversation with Rem Korteweg (Senior Research Fellow, Clingendael Institute).

In this special episode of Our Future Skies - recorded at the IATA Annual General Meeting in Dubai - listen to several leaders as they analyse a range of topics impacting the future of the airline industry, in conversation with John Strickland.

With Scott Kennedy (Senior Advisor and Trustee Chair in Chinese Business and Economics, CSIS (Center for Strategic & International Studies)) and Wendy Cutler (Vice President and Managing Director, Washington, D.C. Office, ASPI (Asia Society Policy Institute)), in conversation with Rem Korteweg (Senior Research Fellow, Clingendael Institute).

Listen to Anders Forslund - Co-founder and CEO, Heart Aerospace – as he offers his perspective on leading with innovation in the aerospace industry, the decarbonisation of air travel, and how infrastructure can boost regional connectivity.

Addressing the challenges of market panel fronting for energy programmes requires a nuanced understanding of legal and regulatory requirements across multiple territories.

In the launch episode of Credit Notes, hear from industry experts as they discuss the dynamics of Trade Finance and complexities of digitisation and technology.

With Victor do Prado (Senior Fellow, Brazilian Center for International Relations – CEBRI), Shannon O'Neil (Vice President of Studies, and Nelson and David Rockefeller Senior Fellow for Latin America Studies, Council on Foreign Relations), in conversation with Rem Korteweg (Senior Research Fellow, Clingendael Institute).

In a lively and wide-ranging conversation, Sir Tim Clark, President of Emirates Airline, shares his unique perspective on the challenges and opportunities ahead for the aerospace industry - from decarbonization and geopolitical turbulence to the shape of future demand and technological change.

With Creon Butler (Director, Global Economy and Finance Programme, Chatham House) and Jennifer Hillman (Professor, IIEL at Georgetown Law; Co-Director of The Center on Inclusive Trade and Development, Georgetown Law), in conversation with Rem Korteweg (Senior Research Fellow, Clingendael Institute).

Listen to expert analysis on the effects of rising sea levels and climate risks on port infrastructure, and the impact on shipping and global trade, in this episode of Navigating Marine Risks.

With Kathleen Claussen (Professor of Law, Georgetown Law) and Simon Evenett (Professor of International Trade and Economic Development, St. Gallen University; Founder of the St. Gallen Endowment for Prosperity Through Trade), in conversation with Rem Korteweg (Senior Research Fellow, Clingendael Institute).

In this episode of Our Future Skies, Marie Owens Thomsen - Senior Vice President Sustainability & Chief Economist, IATA – shares her insights on the impact of technological advances in aviation, the role of evidence-based policy-making, and the challenge of sustainability.

Yvonne Makolo discusses her expert insights on sustainable industry growth, investment in education and training, and the potential of aviation within the African continent.

In this Navigating Marine Risks episode, Stavros Karamperidis and guest experts discuss the impact of the Northern Sea Route on global trade, and the geopolitical dynamics of this emerging shipping connection.

Where does globalisation go from here?

Regional competition or global harmonisation?

Tewolde Gebremariam shares his expert perspectives on aviation infrastructure in Africa, the impact of cargo capacity investments, & leveraging aviation & technological advancements as engines of economic development.

Recorded live from the WTO Public Forum 2023

Trade, conflict and interdependence.

CEO of Pegasus Airlines, discusses her perspective on airline business model development, increasing flexibility for travellers & investing in digital solutions.
Economic, political and supply chain pressures

How trade policy-makers can help tackle global food insecurity

What are the dynamics shaping Southeast Asian trade policies?

A Trade Powerhouse of South America

Sean Doyle, CEO of British Airways, shares his expert views on the agility of the aerospace industry, innovation in sustainability and the new generations of travellers.

In this first episode of Navigating Marine Risks, listen to expert insights and analysis of the human element in shipping, including the welfare and competencies of crew.

Is the Climate Agenda driving a wedge through Global Trade Cooperation?

The opportunities and risks of regionalisation

how organisations can prepare for, respond to and recover from piracy at sea

Paul Griffiths, CEO of Dubai Airports, discusses his long term perspective of the future of airports and the impact of these challenges on the aerospace industry.

Paul Griffiths, CEO of Dubai Airports, discusses his long term perspective of the future of airports and the impact of these challenges on the aerospace industry.

Is the future of global trade regional?

How the global agenda on electronic commerce and digital trade is taking shape

In the second episode of Our Future Skies, Johan Lundgren, CEO of easyJet, shares his insights on the direction of the airline industry over the coming decades, in an in-depth discussion with John Strickland.

How will the midterm elections outcome impact the U.S. approach to trade?

The President & CEO of Scandinavian Airlines System (SAS) provides his future looking perspective on how the many challenges that aerospace faces will result in long term changes to the industry.

The meeting of trade policy and climate policy.

How does international trade impact on women and gender equality?

The digitalisation of trade and the use of credit insurance and capital markets techniques within trade finance make it an attractive asset class for investors, helping narrow the trade finance gap

How are medium powers impacted by the shifting global trading system?

How a decarbonised industry could have a stronger role in future transport and trade.

The past decade has shown a steady year on year rise in securities litigation filed against companies domiciled or headquartered outside of the United States

Simon Evenett Marianne Schneider-Petsinger - Senior Research Fellow, US and the Americas Programme, Chatham House; and Antonio Villafranca - Director of Studies at the Italian Institute of Political Studies (ISPI) discuss the impact of the Ukraine conflict on globalization

Rapid growth in containership size has brought industry concerns over the accumulation of value on mega container vessels, the concentration of value flowing through a limited number of ports and along just a few routes

Hear how organisations can prepare, respond and recover from incidents that require large scale human evacuation.

Podcast: Can the Transatlantic Trade and Technology Council deliver?

Podcast: FTAs, Values and ESG

Podcast: Is the Future Regional?

Podcast: Is trade working for all?

Podcast: US - China relations: when decoupling meets dual circulation

Podcast: Trade integration and the Americas

Podcast: Digital transformation: standards, taxation, and global governance

Podcast: Climate and Trade: on the road to COP26

Transportation is a vital part of the industrial process but one where the environmental risks are often not adequately understood. As a result, there are some in the haulage industry who are operating with uninsured exposures

Podcast: After the pandemic: trade, health and protectionism

Podcast: Trade and the Indo-Pacific: CPTPP, BRI & RCEP

Podcast: Where next for the World Trade Organization and Global Trade Rules?

Podcast: Open Strategic Autonomy

Environmental liabilities present a growing risk to businesses. Heightened levels of public awareness and developing regulation have made businesses more accountable for environmental damage. At the same time, cyber risk is an ever-growing threat to companies of all sizes. The point where the two converge is presenting new challenges.

A hard insurance market has traditionally been a bellwether for captive growth. Previous hard markets have seen existing captive owners make more use of their risk retention vehicles while also driving the formation of new captive solutions

Podcast: How will globalization change?

Podcast: What is the outlook for regional trade integration in Africa?

Podcast: As economies revive, is a surge in protectionism inevitable?

Podcast: Digital Trade: one of the winners?

Reforming the WTO

Podcast: Does the pandemic make an EU-US trade collision less or more likely?

Podcast: The US, China and the EU: the great decoupling?

Podcast: What Now for Sustainable Trade, the Climate Agenda and the Global Trade System?

Podcast: Prospects for a UK-US Trade Deal

Podcast: The Slow Death of Multilateralism

Podcast: Europe’s Evolving Trade Agenda

Despite the market changes of recent months, investor appetite for real estate M&A transactions has held up. However, this type of deal is by no means risk-free and Warranty & Indemnity (W&I) insurance has become a common feature in many markets

Europe’s Trade Strategy for the Age of Geoeconomic Globalization

Three Pillars for a US Trade Strategy in Asia-Pacific

The Geopolitical Impact from a New Wave of Economic Integration

Europe and the Prospects for WTO Reform

Claims data is a wonderful indicator of issues and trends arising out of insured M&A transactions, which is why we invest time and energy in the AIG M&A Claims Intelligence Series

Industrial Subsidies at the Heart of the Trade War

As the US faces off over trade with both China and the EU, expect another year of uncertainty.

Reforming the WTO

The WTO; a membership that pays off

The multilateral trading system is facing a “make or break” moment

The potential benefits of renewable energy sources such as wind, solar, hydro, tidal and geothermal are widely known, including a reduction in greenhouse gas emissions, the diversification of energy supplies and a reduced dependency on fossil fuels.

An established way for non-US companies to provide access for US investors to invest in their shares is for them to issue American Depository Receipts (ADRs). The least regulated ADRs are Level I ADRs which are traded over the counter and not listed on a national exchange such as the NYSE or Nasdaq

Cybercrime is an escalating problem that demands constant attention to mitigate against financial and reputational risk

Cyber is no longer an emerging risk. It is a risk that is already seeing losses – AIG saw as many claims notifications in 2017 as in the previous four years combined, receiving the equivalent of one claim per working day.